
Why supply chain cyber security is essential for resilience
Supply chain cyber security risks have become more complex than ever, with attack surfaces increasing due to the involvement of more suppliers and vendors in sensitive data operations. Consequently, supply chain cybersecurity must adapt to and protect against new infiltration mechanisms, resources, and tools to ensure comprehensive protection across all layers.
Implementing cybersecurity in the supply chain should extend across the entire supplier/partner network, account for cyber threats introduced by advanced manufacturing and IoT, and include security protocol automations.
Expanding on the ‘cyber security joists’ element of our supply chain resilience framework, this article dives into:
- Cyber risks that affect supply chain security
- Essential security control points
- High-priority actions for a robust security management system and strategy
Read on for a detailed discussion on how to mitigate cyber risks and enhance supply chain resilience.
How to enhance cyber security in a supply chain
Supply chain security involves a combination of people, processes, and technology, not only IT. The potential entry points and impact of supply chain security span across procurement, operations, legal and compliance, sourcing, and a number of other functions. To address these risks, a thorough understanding and a shared posture across all the nodes of the supply chain are crucial.
This section will explore the areas manufacturers need to focus on to improve security practices across the supply chain in a coordinated manner.
Cyber resilience: What does it include?
A fully functional cyber security management can be compared to the supply chain’s immune system. It should effectively detect known and potential threats and defend the supply chain from malware, phishing, and other cyber attacks. Like an immune system, transparency and shared security strategies across all nodes of the supply chain are essential.
Modernizing legacy and monolith systems is a necessary prerequisite to minimize the supply chain attack surface area and eliminate easy-to-exploit vulnerabilities. Supply chain cyber security architecture should create a uniform perimeter and be equipped to manage the entire life cycle of security-related events.
In particular, it must:
- Identify potential issues and vulnerabilities by design.
- Protect sensitive and important data at all touch points.
- Detect and defend against potential threats using Security Information and Event Management (SIEM) and machine learning (ML) analytics.
- Respond to the identified anomalies or threats automatically.
- Prevent security breaches and quickly recover from incidents.
Additionally, since each device is a potential threat pathway, identity management plays a crucial role in securing entry points to the systems. A Dynamic talks: Enterprise Security interview with Horacio Zambrano, Cyber Market Strategist from Secret Double Octopus, expands on how to approach identity management and how advanced technologies come into the picture. Read on to learn why a compromised identity of a single device is one of the biggest cyber security risks in the supply chain.
As manufacturers rethink supplier networks and adopt smart manufacturing, potential threat surfaces for cyber attacks will compound. To account for vendors, suppliers, and other third parties, supply chain information security extends to ensuring traceability, and ownership of physical materials and finished goods throughout the supply chain.
How to incorporate cyber security considerations into operations
Manufacturers need to adopt the ‘security is security’ principle and remove the disparity between cyber and physical security. Additionally, the security requirements should be shared with suppliers to address mutual concerns and establish coordinated strategies for addressing security events.
Recommended best practices include adopting the ‘security-by-design’ principle for supply chain IT/OT systems. Operational actions should include:
- Incorporating security requirements into all supplier contract terms, with emphasis on auditing, incident management response, data management practices, and requirements for suppliers’ supply chain partners;
- Building shared recognition of the cyber security posture within the supply network and contractually agreeing on procedures and security controls (such as regular penetration testing);
- Addressing any identified vulnerabilities and security gaps;
- Controlling provenance: from prequalification to quality control;
- Enhancing identity and access management, including escort and audit of software and hardware throughout the supply chain.
Moreover, since diversification of suppliers and the speed of their onboarding is also a factor for building resilience, the recommendation is to automate as much as possible to lower the human error risks. Equally important is to train personnel and ensure that cyber security is an integral part of internal and third-party experience, processes, and tools.
Cyber resilience reinforced with technology
When assessing security practices, the most resilient approach is to assume that cyber defenses will be breached. This shifts the focus from only preventing potential attacks to expanding practices with containment and recovery strategies. This approach increases awareness among employees and leads to faster, more coordinated responses.
Below are key actions to proactively protect the supply chain through the security management system:
- Develop, regularly review, and update cyber security policies and strategies that apply to extended supply chain partners. These should account for, among others:
- Data integrity, encryption, retention, and management;
- Malware protection and detection levels;
- Audit trail of access and data manipulation to prevent unauthorized access and data leaks;
- Regular personnel training.
- Configuration management, quality assurance, and tamper-proofing.
- Embed a zero-trust security model in manufacturing and data collaboration platforms and applications:
- Verify all connections using authorization and authentication of users and devices;
- Implement least privilege principles for need-to-know access to prevent unauthorized access to and exfiltration of data.
- Extend security practices to suppliers: share security protocols and ensure that the extended network has sufficient protection measures and education in place.
- Conduct regular cyber risk assessments for all elements that use IoT devices (storing data, managing inventory, tracking goods).
- Regularly monitor elements with direct access to sensitive data and/or provide a gateway to wider systems.
- Adopt Security Orchestration, Automation, and Response (SOAR) to accelerate incident analysis and responses.
- Use advanced technologies such as Blockchain, SIEM and augmented ML intelligence to minimize discrepancies, detect fraud and intrusion attempts, and ensure the safety and integrity of sensitive data.
- Automate protective measures and security responses for greater transparency and to prevent counterfeit products.
Why cyber security in the supply chain matters
Technology has paved the way for a new era in manufacturing, transforming the flow of information, money, and materials through supply chains. The widespread adoption of cloud solutions and advanced technologies like AI/ML, robotics, IoT, and big data has created an interconnected and collaborative supply chain management landscape.
However, granting third parties, such as suppliers or distributors, access to data and networks, expands the cyber attack surface exponentially. A vulnerability within a single node can compromise the entire supply chain, leading to costly incidents and a disastrous chain reaction. According to the X-Force Threat Intelligence Index report, the manufacturing industry was attacked the most in 2022, accounting for 24.8% of all researched data. Attackers typically target unprotected suppliers or third-party vendors to gain access to larger organizations within the chain.
Supply chain cyber attack examples
Let's look at a few of the most impactful supply chain attacks:
- A cyberattack that affected a plastic and electronic component supplier led to a major supply chain disruption. Toyota, one of the biggest car manufacturers in the world, had to suspend 28 production lines at 14 plants for a day. This suspension significantly impacted supply chain management for car parts and also affected the company's subsidiaries. According to CNN, that one-day pause affected the output of 13,000 vehicles.
- Colonial Pipeline, one of the largest oil pipelines in the US, had paid ~$4,4 million to cyber criminals after being attacked with ransomware. Pipelines were shut down for 5 days, negatively impacting the airline industry and causing panic buying of gasoline.
- NotPetya malware crippled international companies like Maersk, Merck, and FedEx’s subsidiary TNT Express, Reckitt Benckiser, along with countless others. Maersk reported that the cyberattack cost them $300 million in profits.
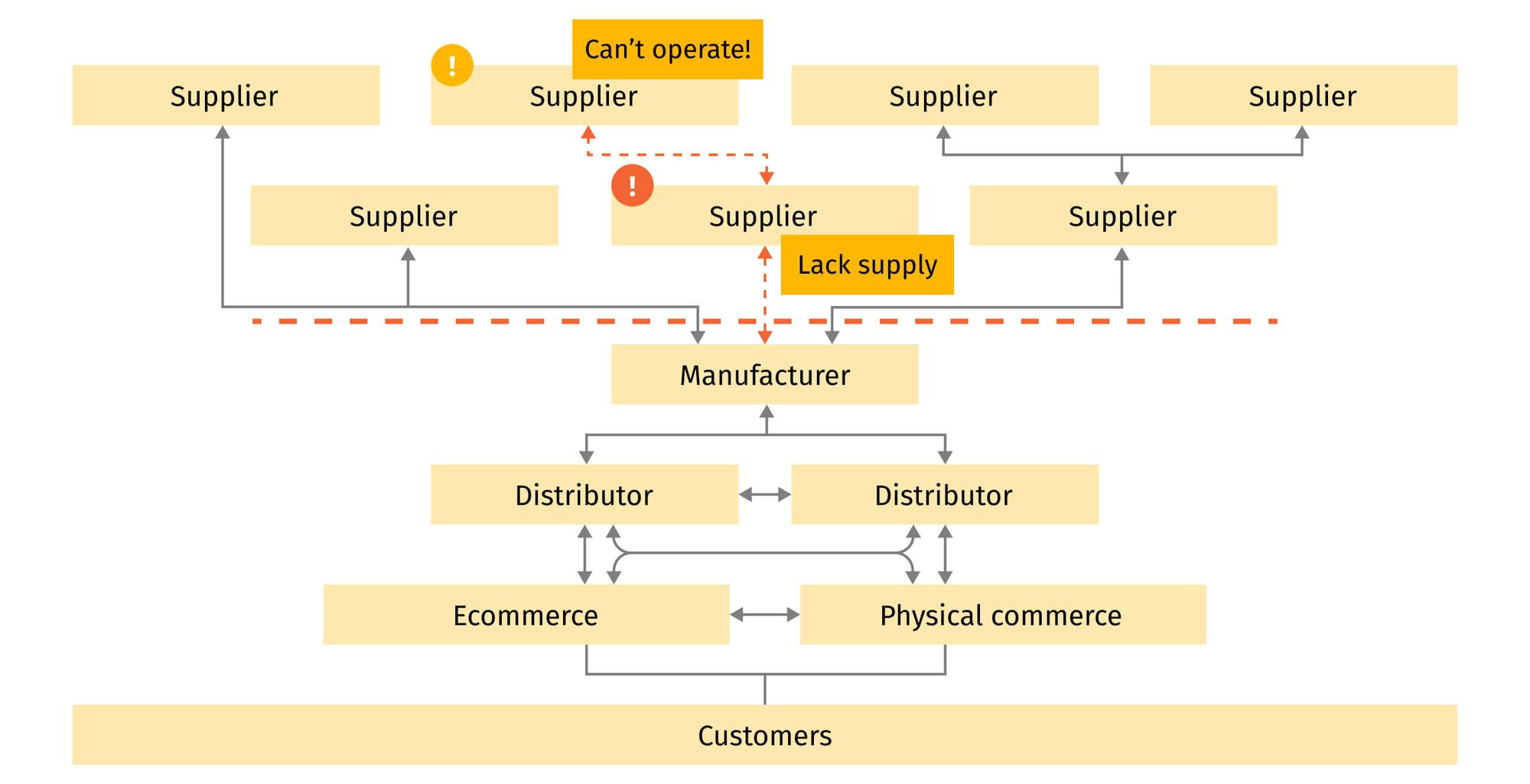
To achieve resilience and efficiently mitigate supply chain risks, a proactive cybersecurity strategy and practices are necessary. The cost of supply chain attacks is not solely financial; they also result in substantial damage to reputation and trust from customers, with impacts extending beyond the incident itself.
Conclusion: Preventing cyber security risks in the supply chain
Implementing cybersecurity in the supply chain safeguards against known vulnerabilities and threat pathways, educates personnel against phishing attempts, and ensures a consistent security posture. Close collaboration with the extended supplier network to consolidate security practices and enhance asset management practices can have a significant impact.
To be resilient, a supply chain should be transparent and easily reconfigurable to respond quickly to potential disruptions. This requires a combination of automated safeguards and comprehensive education and awareness to mitigate evolving cyber threats. Most attacks can be prevented with well-defined and thoroughly followed cybersecurity hygiene. To discuss how cyber security can make your supply chain more resilient, let’s get in touch.
